#cybersecurity #cybersecuritynews
Saigenix aim is to bring awareness and educate people about
Cyber Security.
???????? Daily Cybersecurity News
???? Follow for more updates
Instagram: @saigenix_in
Twitter: @saigenix_in
LinkedIn: www.linkedin.com/in/saigenix
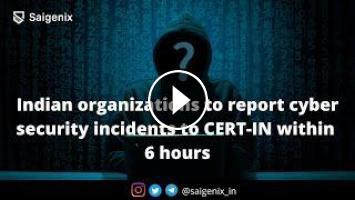
On April 28, 2022, India issued new guidance relating to “information security practices, procedure, prevention, response and reporting of cyber incidents for Safe & Trusted Internet.” The new directives requiring organizations to report cybersecurity incidents to the Indian Computer Emergency Response Team (CERT-IN) within six hours, even if those incidents are port or vulnerability scans of computer systems.
This requirement was promoted by India's Computer Emergency Response Team (CERT-In), who states it has identified specific gaps causing difficulties in security incident analysis and response, and to address them, it needs to impose more aggressive measures. These measures and various other provisions were published via a notice and were integrated into section 70B of the Information Technology (IT) Act, 2000, so they are part of the Indian law, entering into force in 60 days.
Cybersecurity incidents that have to be reported to CERT-In includes:
Targeted scanning/probing of critical networks or systems
Compromise of critical systems or information
Unauthorized access to IT systems or data
Defacement of website or intrusion into a website and inserting malicious code links to external websites
Malicious code attacks
Attack on servers and network devices such as Routers
Identity Theft, spoofing, and phishing attacks
DoS and DDos attacks
Attacks on Critical infrastructure, SCADA and OT systems, and Wireless networks
Attacks on E-Governance, E-Commerce
Data breach or Data leak
Attacks on IoT devices and associated systems, networks, software, servers
Attacks or incidents affecting digital payment systems
Attacks through malicious mobile apps
Fake mobile Apps
Unauthorized access to social media accounts
Attacks or malicious/ suspicious activities affecting cloud computing systems/servers/software/applications
Attacks or malicious/suspicious activities affecting systems/ servers/ networks/ software/ applications related to Big Data, Blockchain, virtual assets, virtual asset exchanges, custodian wallets, robotics, 3D and 4D Printing, additive manufacturing, and drones.
#cybersecurity, #cybercrimes, #cybersecuritynews, #hacking, #security, #technology, #hacker, #infosec, #ethicalhacking, #cybercrime, #tech, #hackers, #cyber, #informationsecurity, #programming, #cyberattack, #kalilinux, #privacy, #malware, #coding, #datasecurity, #dataprotection, #hack, #pentesting, #business, #ransomware, #phishing, #networking, #anonymous, #metasploit, #zomber, #keylogger, #internet, #opensource, #databreach, #dataprivacy, #information, #securityawareness, #spyware, #techreels, #vulnerability, #zerotrustsecurity
Saigenix aim is to bring awareness and educate people about
Cyber Security.
???????? Daily Cybersecurity News
???? Follow for more updates
Instagram: @saigenix_in
Twitter: @saigenix_in
LinkedIn: www.linkedin.com/in/saigenix
On April 28, 2022, India issued new guidance relating to “information security practices, procedure, prevention, response and reporting of cyber incidents for Safe & Trusted Internet.” The new directives requiring organizations to report cybersecurity incidents to the Indian Computer Emergency Response Team (CERT-IN) within six hours, even if those incidents are port or vulnerability scans of computer systems.
This requirement was promoted by India's Computer Emergency Response Team (CERT-In), who states it has identified specific gaps causing difficulties in security incident analysis and response, and to address them, it needs to impose more aggressive measures. These measures and various other provisions were published via a notice and were integrated into section 70B of the Information Technology (IT) Act, 2000, so they are part of the Indian law, entering into force in 60 days.
Cybersecurity incidents that have to be reported to CERT-In includes:
Targeted scanning/probing of critical networks or systems
Compromise of critical systems or information
Unauthorized access to IT systems or data
Defacement of website or intrusion into a website and inserting malicious code links to external websites
Malicious code attacks
Attack on servers and network devices such as Routers
Identity Theft, spoofing, and phishing attacks
DoS and DDos attacks
Attacks on Critical infrastructure, SCADA and OT systems, and Wireless networks
Attacks on E-Governance, E-Commerce
Data breach or Data leak
Attacks on IoT devices and associated systems, networks, software, servers
Attacks or incidents affecting digital payment systems
Attacks through malicious mobile apps
Fake mobile Apps
Unauthorized access to social media accounts
Attacks or malicious/ suspicious activities affecting cloud computing systems/servers/software/applications
Attacks or malicious/suspicious activities affecting systems/ servers/ networks/ software/ applications related to Big Data, Blockchain, virtual assets, virtual asset exchanges, custodian wallets, robotics, 3D and 4D Printing, additive manufacturing, and drones.
#cybersecurity, #cybercrimes, #cybersecuritynews, #hacking, #security, #technology, #hacker, #infosec, #ethicalhacking, #cybercrime, #tech, #hackers, #cyber, #informationsecurity, #programming, #cyberattack, #kalilinux, #privacy, #malware, #coding, #datasecurity, #dataprotection, #hack, #pentesting, #business, #ransomware, #phishing, #networking, #anonymous, #metasploit, #zomber, #keylogger, #internet, #opensource, #databreach, #dataprivacy, #information, #securityawareness, #spyware, #techreels, #vulnerability, #zerotrustsecurity
- Catégories
- E commerce Divers











Commentaires